Hack Router Port 53 Udp
Is this normal or is someone trying to hack/attack me? How can I stop this? My router is a Cg3000v2 netgear provided to me by Optus.
Hack Router Port 53 Udp Dns. 19 Network News Transfer Protocol. 21 Encore Expedited Remote Pro. 23 Network Time Protocol. 24 ANSA REX Trader. 25 Locus PC- Interface Net Map Ser. 26 Unisys Unitary Login. 27 Locus PC- Interface Conn Server. Google Hacking. 7 echo 9 discard 17 qotd 19 chargen 49 tacacs 53 domain 67 dhcps 68 dhcpc 69 tftp 80 http 88. UDP Port Scan with Nmap allows you.
2 Answers
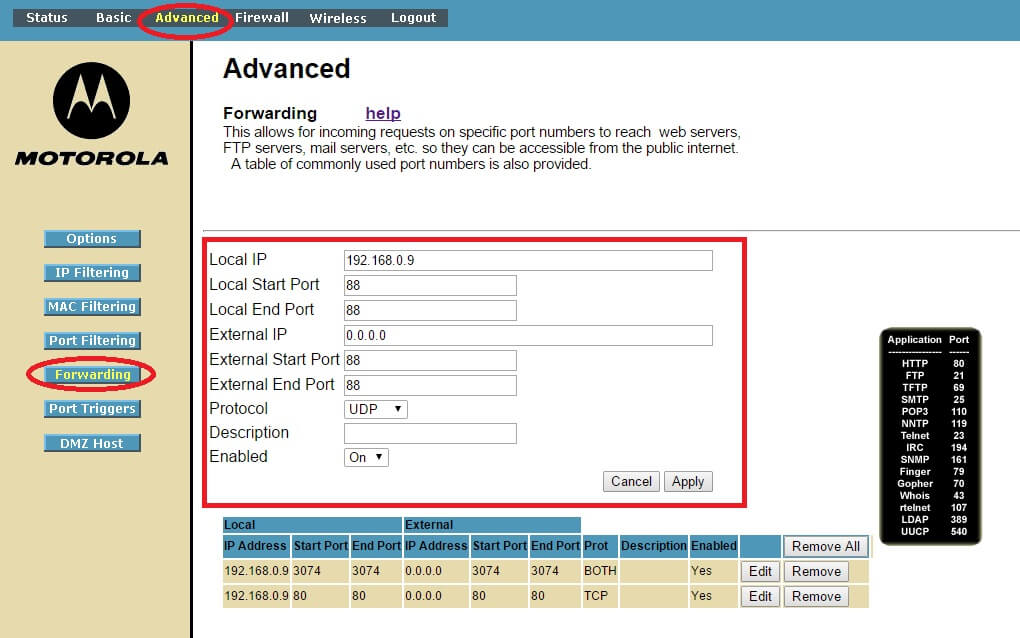
IP Fragmented Packets are a form of evasion against network devices. It consists of submitting the payload through smaller pieces to make it more difficult for firewalls and IPS to identify the scan or even an attack.
Networking scanning is pretty normal and you have to get prepared to it. Important is to have a firewall well configured in place, limit the open ports and have the services listening to them (ports) well hardened.
IP fragmentation attacks are rather old fashioned ones. Your logs show that an attacker has been attempting a denial-of-service (DoS) attack. Note that CheckPoint Firewall-1 was vulnerable to such attacks in its previous versions.
Dns Udp Port 53
That is port scanning. In stealth mode, an attacker can scan the ports over a long period, which reduces the chance that the firewall will trigger an alert for you. Use Nmap, to see what an attacker would see in a port scan of your router.
You need to follow the approach of layered security, no solution is magic by itself, but an intelligent combination of different solutions will protect you better.
Is this normal ?
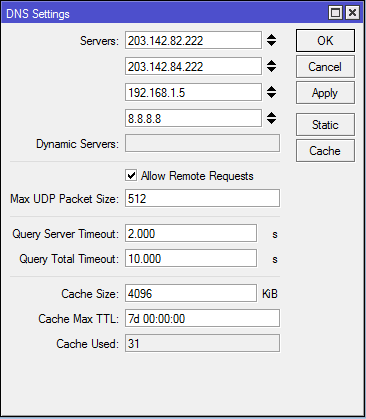
As you may guess, that is not normal.
or is someone trying to hack/attack me?
You have been attacked, for sure. Whether you have been hacked or not, we can not know given the information you provided.
Not the answer you're looking for? Browse other questions tagged networkattacks or ask your own question.
RELATED ARTICLES

How To Open A Router Port
Common ports, such as TCP port 80 (HTTP), may be locked down — but other ports may get overlooked and be vulnerable to hackers. In your security tests, be sure to check these commonly hacked TCP and UDP ports:
TCP port 21 — FTP (File Transfer Protocol)
TCP port 22 — SSH (Secure Shell)
TCP port 23 — Telnet
TCP port 25 — SMTP (Simple Mail Transfer Protocol)
TCP and UDP port 53 — DNS (Domain Name System)
TCP port 443 — HTTP (Hypertext Transport Protocol) and HTTPS (HTTP over SSL)
TCP port 110 — POP3 (Post Office Protocol version 3)
TCP and UDP port 135 — Windows RPC
TCP and UDP ports 137–139 — Windows NetBIOS over TCP/IP
TCP port 1433 and UDP port 1434 — Microsoft SQL Server
